Notable Changes in IE8 Partner Build
If we go on tasting the web browsing via Microsoft Internet Explorer8 RC1 and so on with the coming final version we will see & feel different experience of web browsing as compared to that of with parallel ones available in market. Now let’s have a look on the changes made since Beta2 in RC1 of IE8 Partner Build:
Accessibility-ARIA: The camelCased syntax no longer exists for the ARIA(Accessibility Rich Internet Application) attributes as ARIA attribute names containing dashes, such as “aria-checked”, no longer have to be referenced by their camelCased equivalent (ariaChecked) in IE 7 mode and Quirks mode.
Ajax-XDR: XDR (Cross Domain Request) now checks Access-control-Allow-Origin header for specific URLs as well as wildcards.
Developer Tools: As in previous versions of IE like IE7 and IE8 Beta2 view source application in developer tool was only notepad and built-in viewer respectively. But now user is free to choose developer tool as per requirement via the Developer tool’s menu option. This provides more flexibility to the IE users.
CSS:
• Syntactically valid filter declarations are applied in standards mode, even if unquoted Starting with IE8 Beta 1, the following filter declaration was not applied in standards mode:
filter: progid:DXImageTransform.Microsoft.Alpha(Opacity=80, FinishOpacity=70, Style=2);
Instead, IE8 standards mode required the following declaration:
-ms-filter: “progid:DXImageTransform.Microsoft.Alpha(Opacity=80, FinishOpacity=70, Style=2)”;
For web applications supporting both IE7 and earlier as well as IE8 standards mode, this meant maintaining both declarations and possible a third for other browsers in the case of opacity.
Starting with IE8 Partner Build, the first declaration above will be applied in standards mode if and only if its syntax is valid. If it is not e.g. the final parenthesis is missing then the declaration will not be applied and our CSS parser fails per the standard.
• CSS style sheet encoding detection complies with CSS 2.1 e.g. including @charset directive, charset attribute on link element etc.
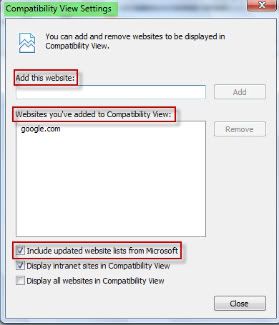
Compatibility View List: A new option for receiving updated lists of websites to be viewed under compatibility view is added under the compatibility view settings but still users can’t avail this facility update Until next release of IE.
 Filter Syntax Property: IE8 will accept the current filter syntax as well as the fully quoted syntax (“-ms” prefix) previously announced for IE8 in the Microsoft CSS Vendor Extension blog post.
Filter Syntax Property: IE8 will accept the current filter syntax as well as the fully quoted syntax (“-ms” prefix) previously announced for IE8 in the Microsoft CSS Vendor Extension blog post.
Links Bar: Now users can customize the title widths of the items on Favorites bar and can place as many items as they want. Via this new option the size of Link bar items can be set to long(default), short(5 chars), or simply favicon.

InPrivate Blocking:
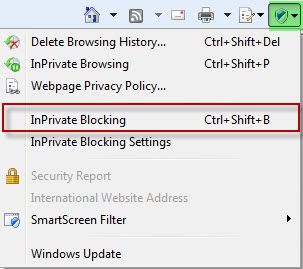
• InPrivate Blocking can be turned on or off via its button present on the status bar.
 • InPrivate Blocking can be turned on or off from Safety Menu’s entry or use keyboard shortcut Ctrl+Shift+B.
• InPrivate Blocking can be turned on or off from Safety Menu’s entry or use keyboard shortcut Ctrl+Shift+B.
 • It is now session-specific as will be off by default each time users launch IE.
• It is now session-specific as will be off by default each time users launch IE.
• InPrivate Blocking can be turned on for all browsing sessions, not just InPrivate Browsing.
• InPrivate Blocking settings dialog UI is improved.
 • New feature first run dialog box.
• New feature first run dialog box.
InPrivate Subscriptions: InPrivate subscriptions have been removed.
InPrivate Browsing: While in InPrivate Browsing Add-ons will be disabled.
Smart Address Bar:
• Typed address count increased(up to 12 default, up to 25 in case History and Favorites are turned off).
• AutoComplete suggestions removed.
• By default Feeds are turned off. In order to turn it on check feeds from AutoComplete Settings dialog in ‘Tools->Internet Options->Content->AutoComplete Settings’.
IEAK8:
• Option “Add to the top of the list” is working now.
• Accelerators can be imported successfully.
• RIES Remove Branding feature has been cut.
Group Policy: To check the functionality now being supported and added open Local Group Policy by typing gpedit.msc in Run dialog box (or in start search bar in Vista). Navigate to ‘User Configuration-> Administrative Templates->Windows Components->Internet Explorer. Functionalities in Group Policy now supported are:
• Turn on Caret Browsing support.
• Turn off Cross Domain Request Object.
• Maximum number of connections per server (HTTP 1.0 and HTTP 1.1) changed from 2 to 128.
• Turn off Compatibility View button.
• Turn off the feeds list.

New Group policies added:
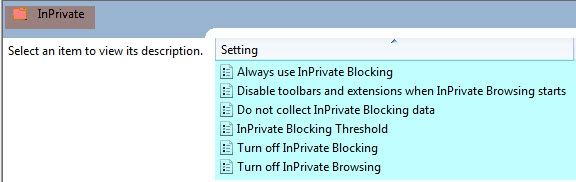
• Always use InPrivate Blocking.
• Do not collect InPrivate Blocking data.
• InPrivate Blocking Threshold.
• Disable toolbars and extensions when InPrivate Browsing starts.
• Disable InPrivate Blocking.
Known Issues:
Compatibility with Facebook:
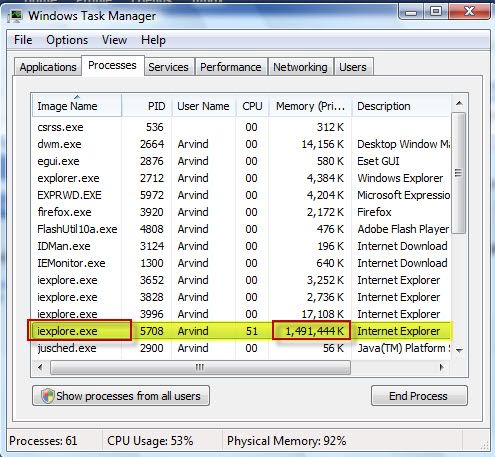
IE8 Partner build has known issue of the Facebook friends list program. The Browser hangs when user uses the “Add to list” box from the friends list. At this time there is no workaround. Here is a view of the issue when the browser hangs and it eats up all the memory of your system so as no other process have room to run smoothly.
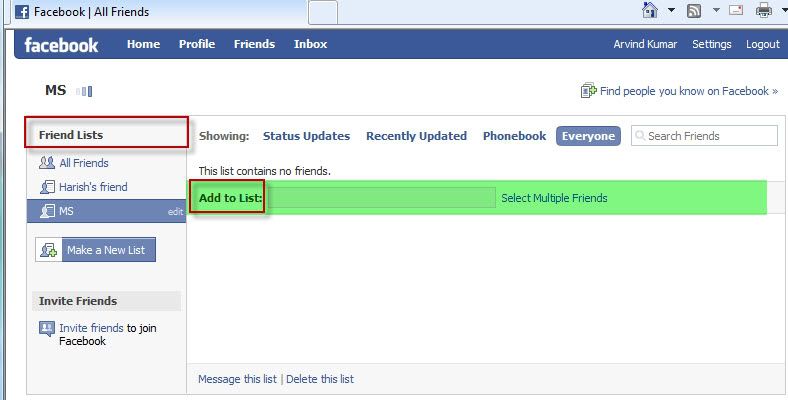
HTTP error which comes after using add to list box in friend list.

Memory eating up by single IE application running only facebook in it s one tab
Password Checker ~ Utility to check the strengths of the passwords
Everybody want to be safe, be secure and the way to remain safe and secure is
to use safe, secure and strong password so as to keep attackers away from safe
locations. But the question is how to create a stron password and then how do
one know that the passwords created by an user is safe or not or whether it is a
strong one or not. So don't worry Microsoft have its solution. The Redmond giant
provides a Password Checker Utility to check the strengths of the passwords.
Solution for creating strong password. Click here.
Solution for getting your passwords strength:
U can easily check strengths of your passwords. Example of Best password from my
view is like "ILuvMyQu@dC()re" it is easy to remember as "ILuvMyQuadCore"
different way. The password checker rates the passwords as Weak, Medium, Strong
and Best.
Password Checker
Windows 7 Beta available for download as early as Jan 5, 2009

The development of Windows 7 is going on and the Beta is at its final stage. Still the delivery deadline date is not confirmed but it is officially confirmed that downloads will be offered via the January 2009 Quarterly Update Kit through the Microsoft Action Pack Subscription (MAPS) from 5th of January.
Participants of the MSDN Developer Conferences will be receiving the DVDs of Windows 7 Beta 1 as early as January 13, 2009. Also the January 2009 kit will contain it along with Microsoft Virtual PC 2007, Windows Small Business Server 2008 Standard Edition, Windows Essential Business Server 2008 Standard Edition, Microsoft Hyper-V Server 2008, Microsoft System Center Data Protection Manager 2007 SP1, and Microsoft System Center Essentials 2007 SP1. The Beta participation program's invitation for testers is started by the Redmond giant for Windows 7 and Windows 7 Server (Windows Server 2008 R2).
WLM 9.0 Beta Refresh down on live
Click here to download the WLM 9.0 Beta Refresh.
Taskkill ~ A Command line utility equivalent of its GUI i.e. Task Manager
Almost all of us came across of situation when Windows Task Manager becomes disabled due to some malware or virus or some other infectious code. At that time we can’t get the details about the processes running and have to take help of some 3rd party tools in order to kill the application or process which is running in background and creating problem in computer system. Instead of using any 3rd party tool we can also play a hand on a command line utility already present in Windows Command Prompt’s command list. This utility is called as Tasklist and Taskkill.
Tasklist: Tasklist is a utility which lists out the currently running processes either on a local computer or on a remote machine. We can easily check which processes are running in background unwillingly and then to terminate such processes we can use Taskkill (explained after tasklist).
Syntax:
tasklist [/s
Parameter description:
/s
/u
/p
/m
/svc :- All service information is listed hosted in each process without truncation. It is only valid when /fo (format) parameter is used.
/v :- Task information is displayed in verbose mode. Parameters /v and /svc are used together in order to display the complete verbose output without truncation.
/fo {table list csv} :- Displays formatted output with default format table. Other valid values are list, csv. csv is the comma separated value format.
/nh :- Valid only for table and csv formats. Used to specify that the “Column Header” not to be displayed in the output.
/fi
Filters description:
Filters are provided to filter the result. This filtering is based on some Filter names which are checked with some relational operators. You will observe that the filter names are the column names which comes in task manager.
Filter Name Valid Operators Valid Values
STATUS eq,ne RUNNINGNOT RESPONDINGUNKNOWN
IMAGENAME eq, ne Name of image
PID eq, ne, gt, lt, ge, le ProcessID number
SESSION eq, ne, gt, lt, ge, le Session number
CPUTIME eq, ne, gt, lt, ge, le CPU time in the format HH:MM:SS, where MM and SS are between 0 and 59 and HH is any unsigned number
MEMUSAGE eq, ne, gt, lt, ge, le Memory usage(in KB)
USERNAME eq, ne Any valid user name (User or Domain\User)
SERVICES eq, ne Service name
WINDOWTITLE eq, ne Window title
MODULES eq, ne DLL name
Points to be noted:
In case of remote process WINDOWTITLE and STATUS filters are not supported.
Examples:
To list all process running without any parameters to list of process with column headers image name, PID, session name & no, and memory usage.
To list all those processes which have PID greater than or equal to 1500 and output in CSV format.
·taskkill /v /fi “PID ge 2151” /fo csv
To list all the processes that are currently in running status under admin account.
·tasklist /fi “USERNAME eq admin” /fi “STATUS eq running”
To list all process on a remote system named serverpc under user name “administrator” having its password as “qu@dc()r3”.
·tasklist /s serverpc /u administrator /p qu@dc()r3
To list all service information for processes having a DLL name beginning with “ntdll”.
·tasklist /m ntdll*
Taskkill: As the name of the utility “taskkill” suggests that it is simply used to see the running processes and to kill one or more processes either by using its PID i.e. ProcessID or by using its Image name i.e. by which it is present in system and being executed. We can also filter the results on the basis of user name, PID, image name, CPU time, memory usage etc at the time of killing or terminating a process.
Syntax:
taskkill [/s
Parameters description:
/s
/u
/p
/fi
/pid >ProcessID> :- For specifying PID of the process to be killed.
/im
/t :- To terminate the whole tree of the process including all child processes started by it.
/f :- For forceful termination of process. It is not omitted in case of remote process as they are terminated forcefully in default.
Filters are provided to filter the result. This filtering is based on some Filter names which are checked with some relational operators. You will observe that the filter names are the column names which comes in task manager.
Filter Name Valid Operators Valid Values
STATUS eq,ne RUNNINGNOT RESPONDINGUNKNOWN
IMAGENAME eq, ne Name of image
PID eq, ne, gt, lt, ge, le ProcessID number
SESSION eq, ne, gt, lt, ge, le Session number
CPUTIME eq, ne, gt, lt, ge, le CPU time in the format HH:MM:SS, where MM and SS are between 0 and 59 and HH is any unsigned number
MEMUSAGE eq, ne, gt, lt, ge, le Memory usage(in KB)
USERNAME eq, ne Any valid user name (User or Domain\User)
SERVICES eq, ne Service name
WINDOWTITLE eq, ne Window title
MODULES eq, ne DLL name
where eq, ne, gt, lt, ge & le are meant for equal to, not equal to, greater than, less than, greater than equal to and less than equal to respectively.
Points to be noted:
In case of remote process WINDOWTITLE and STATUS filters are not supported.
Wildcard (*) character is accepted for /im option only when filter is applied.
Not necessary that /f is specified in case of remote process termination as in default that is terminated forcefully.
Don’t specify computer name to HOSTNAME filter as it will result in a shutdown and all processes are stopped.
For specifying ProcessID (PID) tasklist command can be used.
Examples:
To terminate a process with PID 3276 use parameter /pid.
·taskkill /pid 3276
To terminate more than one process with pid as 2001, 2224, 4083.
·taskkill /pid 2001 /pid 2224 /pid 4083
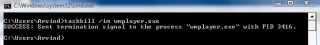
To terminate a process with its image name like wmplayer.exe for Windows Media Player use /im parameter.
·taskkill /im wmplayer.exe
To terminate a process and all its child process i.e. to end process tree in task manager use /t parameter. ·taskkill /f /im explorer.exe /t
To terminate all those processes which have PID greater than or equal to 1500 without considering their image names use filter ge with wildcard character.
·taskkill /f /fi “PID ge 1500” /im *
To terminate the process tree with PID 2521 which is started by account name admin.
·taskkill /pid 2521 /t /fi “USERNAME eq admin”
To terminate all process beginning with note on a remote system named serverpc under user name “administrator” having its password as “qu@dc()r3”.
·taskkill /s serverpc /u administrator /p qu@dc()r3 /fi “IMAGENAME eq note*” /im *
To terminate a process with its windows title as “paint”
·taskkill /f /fi “WINDOWTITLE eq paint”
Creating Strong Paasword ~ Way to remain safe from threats!
Passwords are considered as first line of defense against unauthorized access to computer. Remember strong is the password more the computer is protected from hackers and malwares.
• Is at least eight characters long.
• Does not contain your user name, real name, or company name.
• Does not contain a complete word.
• Is significantly different from previous passwords.
• Contains characters from each of the following four categories:
Character category
Uppercase letters like A, B, C
Lowercase letters like a, b, c
Numbers like 0, 1, 2, 3, 4, 5, 6, 7, 8, 9
Symbols found on the keyboard (all keyboard characters not defined as letters or numerals) and spaces like ` ~ ! @ # $ % ^ & * ( ) _ - + = { } [ ] \ : ; " ' < > , . ? /
A password might meet all the criteria above and still be a weak password. For example, Hello2U! meets all the criteria for a strong password listed above, but is still weak because it contains a complete word. H3ll0 2 U! is a stronger alternative because it replaces some of the letters in the complete word with numbers and also includes spaces.
Have a glance of following tips which will help in remembering string passwords:
• Use easy-to-remember piece of information to create acronyms as for example pick some meaningful phrases to use as your guide. Then create passwords using that phrases as My Birthday is on 23 February, 1987 which might be used as Mbio23/Feb,87.
• Create an acronym from an easy-to-remember piece of information. For example, pick a phrase that is meaningful to you, such as My son's birthday is 12 December, 2004. Using that phrase as your guide, you might use Msbi12/Dec,4 for your password.
• Substitute numbers, symbols, and misspellings for letters or words in an easy-to-remember phrase. For example, My son's birthday is 12 December, 2004 could become Mi$un's Brthd8iz 12124 (it's OK to use spaces in your password).
• Relate your password to a favorite hobby or sport. For example, I love to play badminton could become ILuv2PlayB@dm1nt()n.If you feel you must write down your password in order to remember it, make sure you don't label it as your password, and keep it in a safe place.
Windows Registry Startup paths
Various Paths to Launch Programs at Startup:-
1. Via Start up folder. First enable show hidden files option and then navigate to any of the following paths and Add shortcuts of the programs to be run at start up.
C:\Users\[USERNAME]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup ( In Vista )
C:\Documents and Settings\YourUserName\Start Menu\ Programs\Startup ( In XP )
C:\ Users\AllUsers\ AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup ( In Vista )
C:\Documents and Settings\AllUsers\Start Menu\ Programs\Startup ( In XP )
2. Via Registry. Navigate to any of the following path according to your requirement and then add a new “String key” and store path of the Program to be run in this key’s value.
For Local Machine-
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
For Current User-
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
3.Programs to run at logon time or when explorer runs. Navigate to path HKEY_LOCAL_MACHINE\Software\Microsoft\WindowsNT\CurrentVersion\WinLogon\ and add path of your program to be run as follows.
· Via Shell String as by editing value of key “Shell” as explorer.exe,
· Via Userinit String as by editing value of key “Userinit” as C:\Windows\System32,,
New IE8 Build Available for Tech Beta Participants

Technet Subscriber can direclty download the IE 8 new build release via Microsoft connect and it seems that its RC is on its way to come in early 2009.
Way to avoid online donation scams
How to spot it:
One form of fraud is phishing in which spamming is done by fraudulent spam e-mail messages, online forum posts like unwanted things asks funds in the name of well-known legitimates charities or for victims of disasters. These spams’s pop up while working on Internet and may steal money or personal information by providing links to some phony websites seems to be official.
Avoiding steps:
- Use Microsoft Phishing Filter.
- Be with technology and improve security of your computer.
- Directly contact to the well established and known charity agencies that are used before by you or by other trusted person rather than responding to solicitations.
- Ensure the legitimate site certificates and written policy of protecting personal information before providing credit card number or other personal information to any charity related Website.
- Never reveal your personal information or click on any unsolicited e-mail received from any charitable organization asking for money.
- Instead of clicking on e-mail request from charity for donation go to their Website by manually address in browser or simply call them for verification and ask the procedure of contribution.
- Make habit of typing address of organizations during working online.
- Usually spoofed Websites deceive users by using deliberate, easily overlooked misspellings so always double-check the spelling of Websites and be habitual of looking at actual address before further steps while browsing Internet.
- Beware of the photos of disaster victims or areas attached s they may be infected with computer viruses.
- Keep up to date information of online scams from some professional sources, trusted technology news providers or government agencies.
Signs of Spyware
Pop ups popping up all the time: If any pop up ads not related with the website being visited by you bombards which are often of any adult or other website. You may get them at the time you logon or even not browsing web, it seems to be sign of some spyware or unwanted software.
Settings changed and can’t reset: Some time the home page or search page settings are changed and even if way to make them correct is known can’t be done or changes back when system restarts.
Add-ons installed without user knowledge: Additional toolbars are added to the web browser without any need that can’t be removed and even if you managed to remove them you saw them again there after a reboot.
Computer goes slow: The reason behind the computer’s slow performance is the spywares and unwanted software which uses resources in order to track your activities and deliver ads. This may lead to computer crash in case of error in the software.
System might be affected with spyware or other unwanted software if the count of crashes increases or it responds slower than normal.
View new generation Windows Live
Lifestyle on the Windows Live is going to change to a new sleek n exciting view and home.live.com will be the home base for all Windows Live users. The online place for sharing photos, files, chat with IM, email, connect to your favorite people and many more activities. The updated Windows Live online services and new product betas will help you stay in touch, share your stuff, and keep your life in sync... even better than before.
The betas for your PC of the Windows Live Products are available for download at Live.
Press Space Bar in Se7en for Windows Boot Manager
In Windows 7 pressing F8 will move system in recovery console option. This option can also be tried at the time of booting via Vista or Server's disk.
Privacy Statement
If you choose not to provide personal information, you can still use most of the features on the website, but you will not be able to comment and subscribe daily newsletter or areas that require your personal details.
unlockwindows.com strictly protects the security of your personal information and honors your choices for its intended use. We carefully protect your data from loss, misuse, unauthorized access or disclosure, alteration, or destruction.
Distribution of personal information UnlockWindows.com does not distribute personal information to any third parties. Should this change, UnlockWindows.com will not distribute any information without your prior express consent.
If for some reason you believe UnlockWindows.com have not adhered to these principles, please notify us by Email at arvind[dot]windows[at]hotmail[dot]com, and we will do our best to determine and correct the problem promptly.
Changes to this documentChanges to this document may be made any time without warning. UnlockWindows.com may or may not notify you of changes in this policy, however, we will make an effort to notify you if there are any major changes to this policy. You will not be notified about changes related to clarification and/or elaboration of parts of this policy.
Term of Use
2.You must give credits unlockwindows.com when you quote and link to the exact article URL, from where the information has taken.
3.When you have done, we request you to send us your article link via mailing to Arvind.windows@hotmail.com. We take plagiarism very seriously. If we find any website / blog / forum republishing our website content / RSS feeds illegally, we’ll take a legal action immediately.
TrademarksMicrosoft and its products are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries.
Windows is registered trademark of Microsoft Corporation, and is being used for identification purpose only.
Other Trademarks are the properties of their respective owners.
Reporting Copyright InfringementsIf you believe that any copyright infringement exists on this Website, send us Email along with the URL. It would be dealt with utmost care. We want to be as fair as we can.
Copyright Policy
1.You are allowed to post a short excerpt or pick up to 4-5 lines of the article at from UnlockWindows.com. You are not allowed to post full article.
2.You must give credits UnlockWindows.com when you quote and link to the exact article URL, from where the information has taken.
3.When you have done, we request you to send an email to us including your article link at arvind[dot]windows[at]hotmail.com.
We take plagiarism very seriously. If we find any website / blog / forum republishing our website content / RSS feeds illegally, we’ll take a legal action immediately.
Trademarks
Microsoft and its products are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries.
Windows is registered trademark of Microsoft Corporation, and is being used for identification purpose only.
Other Trademarks are the properties of their respective owners.
Reporting Copyright Infringements
If you believe that any copyright infringement exists on this Website, send us Email at arvind[dot]windows[at]hotmail.com along with the URL. It would be dealt with utmost care. We want to be as fair as we can.
"Unlock-Windows"
This is Arvind Kumar from India, currently doing B.Tech from JECRC, Jaipur. Today I'm going to introduce first Microsoft Windows based weblog. Here you can find registry tweaks, tips-n-tricks, guides, tutorials, latest trends of IT, Windows customization including themes, wallpapers etc. and much more !!!
"Unlock-Windows" as title suggesting, here you can find information to unlock or customize your Windows operating system according to your business and interest. Apart from all these things, you may find some more useful information about Microsoft products such as Windows Server, Visual Studio suites, Windows Live, Microsoft Office n so on and their fast track manuals and guides.
So "What are you waiting for ?" here we go...
Sincerely
Arvind Kumar
arvind.windows@hotmail.com
Unlock Windows
Search
Subscribe
Translator
Popular Posts
Blog Archive
- March 2011 (3)
- February 2011 (2)
- January 2011 (4)
- December 2010 (13)
- November 2010 (7)
- October 2010 (7)
- September 2010 (1)
- August 2010 (2)
- July 2010 (3)
- June 2010 (8)
- May 2010 (18)
- April 2010 (12)
- March 2010 (15)
- February 2010 (9)
- January 2010 (15)
- December 2009 (21)
- November 2009 (28)
- October 2009 (35)
- September 2009 (14)
- August 2009 (23)
- July 2009 (19)
- June 2009 (20)
- May 2009 (12)
- April 2009 (18)
- March 2009 (8)
- February 2009 (7)
- January 2009 (14)
- December 2008 (16)
Labels
- Anti Virus
- Apple
- Beta Products
- Bing
- Bugs
- Creativity
- Download Center
- Ebooks
- Events
- Expression
- Games
- Internet Explorer
- Keyboard Shortcuts
- Microsoft Hardware
- Microsoft Office
- Microsoft Research
- News
- Offers
- Review
- Security
- Silverlight
- Software
- SQL Server
- Themes
- Tips 'n' Tricks
- Unsorted
- Visual Studio
- Wallpapers
- Windows 7
- Windows 8
- Windows Live
- Windows Mobile
- Windows Phone
- Windows Server
- Windows Vista
- Windows XP
- Zune
Friends
About Me
- Arvind Kumar
- I'm Arvind Kumar from India, B.Tech, now working in a MNC. I love to use Microsoft Products and learn from that. Bill Gates is my ideal person.